Aircrack Check Your Essid
Idea and initial work: ASPj Additions by: a number of good souls Last updated: May 09, 2008 This tutorial will give you the basics to get started using the aircrack-ng suite. It is impossible to provide every piece of information you need and cover every scenario. So be prepared to do some homework and research on your own. The and the have lots of supplementary tutorials and information. File video download.
Jul 26, 2017 Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat. This is a brief walk-through tutorial that illustrates how to crack Wi-Fi networks that are. Apr 25, 2013 - -9 means injection test. Long form is - -test. -e teddy is the network name (SSID). This is optional. -a 00:de:ad:ca:fe:00 ath0 is MAC address of the access point (BSSID). This is optional. -i wlan1 is interface name of the second card if you want to determine which attacks your card supports. This interfaces. Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat. This is a brief walk-through tutorial that illustrates how to crack Wi-Fi networks that are secured using weak passwords.
Essid Wireless Configuration
Although it does not cover all the steps from start to finish like this tutorial, the tutorial covers the actual aircrack-ng steps in much more detail. Setting up Hardware, Installing Aircrack-ng. The first step in getting aircrack-ng working properly on your Linux system is patching and installing the proper driver for your wireless card. Many cards work with multiple drivers, some of which provide the necessary features for using aircrack-ng, and some of which do not. Needless to say, you need a wireless card which is compatible with the aircrack-ng suite. This is hardware which is fully compatible and can inject packets. A compatible wireless card can be used to crack a wireless access point in under an hour.
To determine to which category your card belongs to, see. Read if you don't know where to look in this table. It still does not hurt to read this tutorial to build your knowledge and confirm your card attributes. First, you need to know which chipset is used in your wireless card and which driver you need for it. You will have determined this using the information in the previous paragraph. The will tell you which drivers you need for your specific chipset.
Download them and then get the corresponding patch from. (These patches enables the support for injection.) As I own a Ralink USB device, I am providing the steps to get it working with Aircrack-ng.
Before you are able to compile and install drivers, you need the kernel-sources for your distribution installed. If you own another type of card, check the for instructions about other drivers. As well, do a search in the net if you're unsure how to install them.
RaLink USB rt2570 Setup guide. If you own a rt2570 USB device (like D-Link DWL-G122 rev. B1 or Linksys WUSB54G v4) you should use the drivers from These are special modified drivers, which support injection and are reported to work best with Aircrack-ng. They don't need to be patched. Of course these drivers do also work for normal operation. (Starting with kernel 2.6.25 and Aircrack-ng v1.0-rc1, the in-kernel driver, rt2500usb, can also be used.) Lets unpack, compile and install the drivers: tar xfj rt2570-k2wrlz-1.3.0.tar.bz2 cd rt2570-k2wrlz-1.3.0/Module make make install The last step has to be performed as root.
Use su to change to root. Now we can load the module into the kernel: modprobe rt2570 Plug in your card, it should be recognized as rausb0 now. Run iwconfig to list your wireless devices and check if everything is working. Aircrack-ng installation. Currently, neither of the repositories hosts the latest version of Aircrack-ng. It's recommended that you use the first method instead. If you are using a system which is rpm-based then you can take the easy way to install aircrack-ng.
(Example for Redhat Linux 4) su rpm -ihv IMPORTANT: Check for the latest version of the aircrack-ng suite and change the command above to reference the latest version. IEEE 802.11 basics. Ok, now everything is ready, time to make a pit stop before the action finally starts and learn something about how wireless networks work. The following chapter is very important, if something doesn't work as expected. Knowing what all is about helps you find the problem or helps you at least to describe it so someone else who can help you.
This is a little bit scientific and maybe you feel like skipping it. However, a little knowledge is necessary to crack wireless networks and because it is a little more than just typing one command and letting aircrack do the rest. How a wireless network is found.
Which channel the network is on This information is then shown in your tool that connects to this network. It is shown when you let your card scan for networks with iwlist scan and when you run. Every AP has a unique MAC address (48 bit, 6 pair of hexadecimal numbers).
It looks like 00:01:23:4A:BC:DE. Every network hardware device has such an address and network devices communicate with each other by using this MAC address. So its basically like a unique name. MAC addresses are unique, no two network devices in the world have the same MAC address.
Connecting with a network. The first thing to do is looking out for a potential target. The aircrack-ng suite contains for this - but other programs like can be used too. Prior to looking for networks, you must put your wireless card into what is called “monitor mode”. Monitor mode is a special mode that allows your PC to listen to every wireless packet.
This monitor mode also allows you to optionally inject packets into a network. Injection will be covered later in this tutorial.
To put your wireless card into monitor mode: start rausb0 To confirm it is in monitor mode, run “iwconfig” and confirm the mode. The on the Wiki has generic information and how to start it for other drivers.
Then, start airodump-ng to look out for networks: airodump-ng rausb0 “rausb0” is the network interface (nic) name. If you are using a different WLAN device than a rt2570 you'll have to use a different nic name.
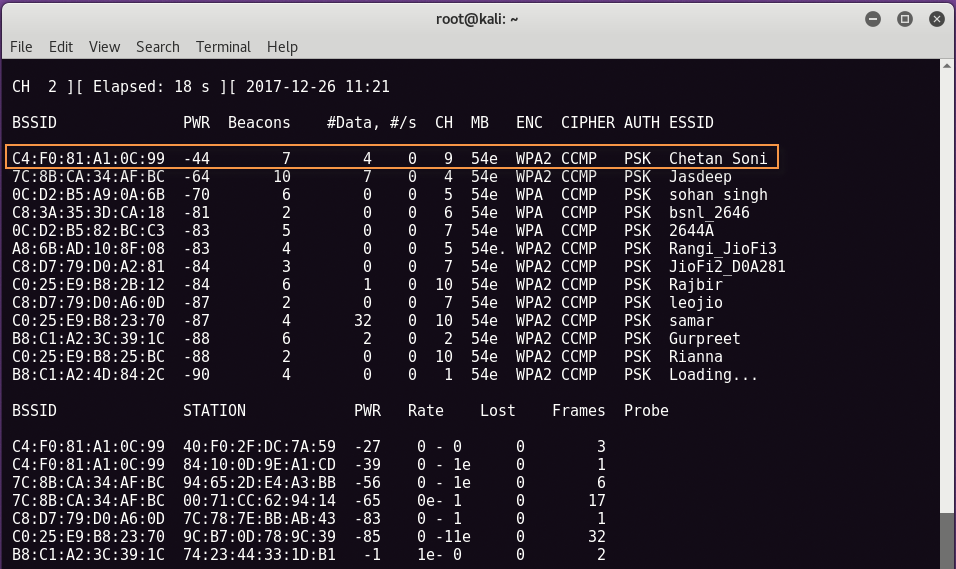
Take a look in the documentation of the nic driver. For most newer drivers, the primary interface name is “wlan0”, but for monitoring, a secondary interface (“mon0”, created when you run airmon-ng) is used. If airodump-ng could connect to the WLAN device, you'll see a screen like this: hops from channel to channel and shows all access points it can receive beacons from.
Channels 1 to 14 are used for 802.11b and g (in US, they only are allowed to use 1 to 11; 1 to 13 in Europe with some special cases; 1-14 in Japan). Channels between 36 and 149 are used for 802.11a. The current channel is shown in the top left corner. After a short time some APs and (hopefully) some associated clients will show up. The upper data block shows the access points found. BSSID The MAC address of the AP PWR Signal strength. Some drivers don't report it Beacons Number of beacon frames received.
If you don't have a signal strength you can estimate it by the number of beacons: the more beacons, the better the signal quality Data Number of data frames received CH Channel the AP is operating on MB Speed or AP Mode. 11 is pure 802.11b, 54 pure 802.11g. Values between are a mixture ENC Encryption: OPN: no encryption, WEP: WEP encryption, WPA: WPA or WPA2 encryption, WEP?: WEP or WPA (don't know yet) ESSID The network name.
Sometimes hidden The lower data block shows the clients found. BSSID The MAC of the AP this client is associated to STATION The MAC of the client itself PWR Signal strength. Some drivers don't report it Packets Number of data frames received Probes Network names (ESSIDs) this client has probed Now you should look out for a target network. It should have a client connected because cracking networks without a client is an advanced topic (See ). It should use WEP encryption and have a high signal strength. Maybe you can re-position your antenna to get a better signal.
Often a few centimeters make a big difference in signal strength. In the example above the net 00:01:02:03:04:05 would be the only possible target because it's the only one with an associated client. But it also has a high signal strength so it's really a good target to practice.
Sniffing IVs. Because of the channel hopping you won't capture all packets from your target net. So we want to listen just on one channel and additionally write all data to disk to be able to use it for cracking: airodump-ng -c 11 -bssid 00:01:02:03:04:05 -w dump rausb0 With the -c parameter you tune to a channel and the parameter after -w is the prefix to the network dumps written to disk. The “- -bssid” combined with the AP MAC address limits the capture to the one AP. The “- -bssid” option is only available on new versions of airodump-ng. Before being able to crack WEP you'll usually need between 40 000 and 85 000 different Initialization Vectors (IVs). Every data packet contains an IV.
IVs can be re-used, so the number of different IVs is usually a bit lower than the number of data packets captured. So you'll have to wait and capture 40K to 85K of data packets (IVs). If the network is not busy it will take a very long time. Often you can speed it up a lot by using an active attack (=packet replay). See the next chapter. If you've got enough IVs captured in one or more file, you can try to crack the WEP key: aircrack-ng -b 00:01:02:03:04:05 dump-01.cap The MAC after the -b option is the BSSID of the target and dump-01.cap the file containing the captured packets. You can use multiple files, just add all their names or you can use a wildcard such as dump.cap.
For more information about parameters, description of the output and usage see the. The number of IVs you need to crack a key is not fixed. This is because some IVs are weaker and leak more information about the key than others. Usually these weak IVs are randomly mixed in between the stronger ones.
So if you are lucky, you can crack a key with only 20 000 IVs. But often this it not enough and aircrack-ng will run a long time (up to a week or even longer with a high fudge factor) and then tell you the key could not be cracked. If you have more IVs cracking can be done a lot faster and is usually done in a few minutes, or even seconds.
Experience shows that 40 000 to 85 000 IVs is usually enough for cracking. There are some more advanced APs out there that use an algorithm to filter out weak IVs. The result is either that you can't get more than “n” different IVs from the AP or that you'll need millions (like 5 to 7 million) to crack the key. Search in the, there are some threads about cases like this and what to do. Active attacks. Most devices don't support injection - at least not without patched drivers.
Some only support certain attacks. Take a look at the, column aireplay. Sometimes this table is not up-to-date, so if you see a “NO” for your driver there don't give up yet, but look at the driver homepage, the driver mailing list or our. If you were able to successfully replay using a driver which is not listed as supported, don't hesitate to update the table and add a link to a short howto. (To do this, request a wiki account on IRC.) The first step is to make sure packet injection really works with your card and driver. The easiest way to test it is the attack. Make sure to perform this test prior to proceeding.
Your card must be able to successfully inject in order to perform the following steps. You'll need the BSSID (AP MAC) and ESSID (network name) of an AP that does not do MAC filtering (e.g. Your own) and must be in range of the AP.
Try to connect to your AP using: aireplay-ng -fakeauth 0 -e 'your network ESSID' -a 00:01:02:03:04:05 rausb0 The value after -a is the BSSID of your AP. If injection works you should see something like this: 12:14:06 Sending Authentication Request 12:14:06 Authentication successful 12:14:06 Sending Association Request 12:14:07 Association successful:-) If not. First open a window with an sniffing for traffic (see above). And can run together. Wait for a client to show up on the target network. Then start the attack: aireplay-ng -arpreplay -b 00:01:02:03:04:05 -h 00:04:05:06:07:08 rausb0 -b specifies the target BSSID, -h the MAC of the connected client. Now you have to wait for an ARP packet to arrive.
Usually you'll have to wait for a few minutes (or look at the next chapter). If you were successful, you'll see something like this: Saving ARP requests in replayarp-0627-121526.cap You must also start airodump to capture replies. Read 2493 packets (got 1 ARP requests), sent 1305 packets.
If you have to stop replaying, you don't have to wait for the next ARP packet to show up, but you can re-use the previously captured packet(s) with the -r option. When using the arp injection technique, you can use the PTW method to crack the WEP key. This dramatically reduces the number of data packets you need and also the time needed.
You must capture the full packet in airodump-ng, meaning do not use the “- -ivs” option when starting it. For, use “aircrack -z ”. (PTW is the default attack in 1.0-rc1.) If the number of data packets received by airodump-ng sometimes stops increasing you maybe have to reduce the replay-rate. You do this with the -x option. I usually start out with 50 and reduce until packets are received continuously again. Better positioning of your antenna usually also helps.
The aggressive way. Most operating systems clear the ARP cache on disconnection. If they want to send the next packet after reconnection (or just use DHCP), they have to send out ARP requests. So the idea is to disconnect a client and force it to reconnect to capture an ARP-request. A side-effect is that you can sniff the ESSID and possibly a keystream during reconnection too.
This comes in handy if the ESSID of your target is hidden, or if it uses shared-key authentication. Keep your airodump-ng and aireplay-ng running. Open another window and run a attack: aireplay-ng -deauth 5 -a 00:01:02:03:04:05 -c 00:04:05:06:07:08 rausb0 -a is the BSSID of the AP, -c the MAC of the targeted client. Wait a few seconds and your arp replay should start running. Most clients try to reconnect automatically. But the risk that someone recognizes this attack or at least attention is drawn to the stuff happening on the WLAN is higher than with other attacks. Further tools and information.
So I wanted to show users how to sniff out their local wireless traffic, capture it and decrypt it. However, before I made up a long winded post I decided to research it, see if someone else has done the work already. Sure enough someone has, so take a look at the following. The article is geared for identifying wireless security holes and exploting them. But i’ll let you read the rest.
It’s not advanced stuff, you can learn more about in still interested. I’ve copied the posters conents here, if you don’t want to deal with the. If you want the screenshots, you’l have to sign into the forums. GENERAL INFORMATION: Generally speaking there are 3 types of attacks: 1.
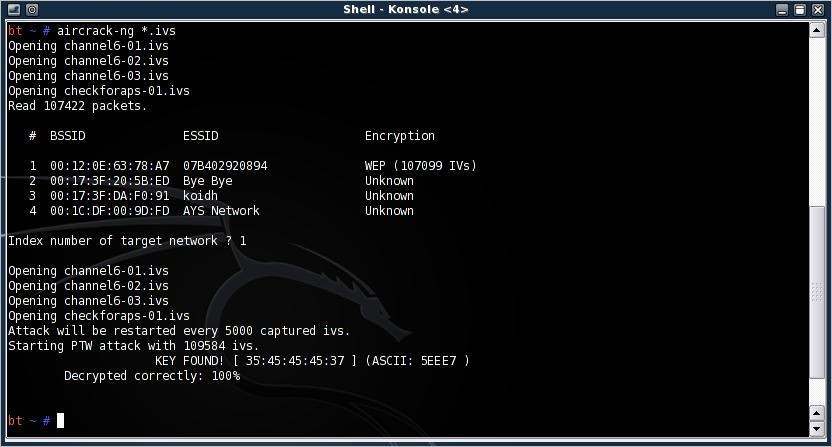
Brute force attack 2. Dictionary attack 3. Statistical attack By exploiting several security weaknesses of the WEP protocol Aircrack NG makes use of a statistical method to recover WEP keys. Provided that you have collected a sufficient number of IVs (= Initialization Vectors) and depending on the length of the encryption key, determining the actual WEP key will take less than a minute on a common PC.
HARDWARE: I assume that you have successfully patched the driver for your wireless adapter (e.g. Ralink chipset), so I won’t go into this.
I have tested packet injection and decryption with: 1. Intel® PRO/Wireless 2200BG (IPW2200) 2. Linksys WUSB54G V4.0 (RT2570) I recommend “Linksys WUSB54G V4.0” as it has a decent reception and reasonable performance. If you need help patching & compiling from source, feel free to post your problems here as well.
DRIVERS & PATCHES: Before you proceed you need to compile your own drivers & install patches for packet re-injection. You find instructions.
PREREQUISITES: 1. You have successfully patched your wireless driver (see link above). This HOWTO was written for Aircrack-NG v0.9.1 & Aircrack-PTW v1.0.0 on Kubuntu Feisty Fawn 7.04 (32-bit). ’00:09:5B:D7:43:A8′ is the MAC address of my network, so you need to replace it with your own. ’00:00:00:00:00:00′ is the MAC address of the target client, NOT that of your own wireless card. COMMAND LINE: Please make sure that you stick to the exact sequence of actions and pay attention to section on MAC filtering.
Enable monitoring with “airmon-ng” (screenshot #1):. Quote: sudo aireplay-ng -3 -b 00:09:5B:D7:43:A8 -h MY:MA:CA:DD:RE:SS You’ll now see the number of data packets shooting up in ‘airodump-ng’. This process can take up to five minutes before you start receiving any ARP requests. So be a little patient at this point. As MAC filtering is off, use an arbitrary MAC address (‘MY:MA:CA:DD:RE:SS’). Continue with #6. NOTE: -3 Standard ARP-request replay.b MAC address of target access point.h MAC address of your choice.
MAC filtering. Actually, the average user isn’t going to know that your snooping. All wireless traffic is out in the open. The safeguard we use is to encrypt the transmissions via WEP, WPA, WPA2,etc Once you get a hold of those keys then you can intercept the traffic after it leaves the router while on it’s way to the users device. They won’t know that it’s been breached, the only safeguard You can take to make sure your wifi traffic is secure is to use the highest form of encryption available with a very very strong 128 + key over 10 characters,(alpha-numeric), Also DISABLE your SSID broadcast, believe it or not that’s the 1st big step to veer away any snoops.